Home » Investors » Corporate Governance » Corporate Governance Practices » Information Security Organization Management
Corporate Governance Practices
Information Security Organization Management
In order to effectively implement the Company’s information security management, the Company has set up an information security team, with the CRO acting as the convener, and under which there are the information security response center and the information security implementation team, responsible for the information security management, planning, supervision, and execution facilitation to reduce the Company’s operation and information security risks. In order to implement the information security maintenance plan, the Company has added an information security audit team in 2023.
The Information Security Committee shall meet regularly each year to review and examine the implementation of the Company’s information security management policies and report its findings to the Board of Directors. The last report was made on November 2, 2023.
Information security audit team:
It shall be assigned by the Information Security Committee or assisted by a third party to evaluate the implementation of the information security management system.
Information Security Organizational Structure and Job Responsibilities:
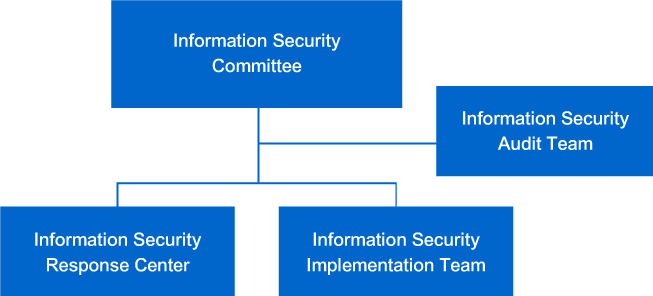
(1) Information Security Committee:
The CRO shall act as the convener of the committee, and the Information Security Response Center and the Information Security Implementation Team set under the committee are responsible for the implementation of resolutions related to the information security management system.
(2) Information Security Implementation Team:
The team is composed of the personnel assigned by the convener of the Information Security Committee that is responsible for planning and implementing various information security works.
(3) Information Security Response Center:
The Center is responsible for responding to unexpected information security events with corresponding solutions, as well as tracking collection and event identification. The “Risk Improvement Plan” shall be prepared, controlled, and tracked continuously until the improvement.
(4) Information security audit team:
It shall be assigned by the Information Security Committee or assisted by a third party to evaluate the implementation of the information security management system.
Information Security Policies and Specific Management
For the purposes of improving the security and stability of the Company’s information and communication, providing reliable information services, including the security precautions that must be controlled when using the network and information systems, preventing operational risks and hazards such as improper use, disclosure, tampering, and destruction of the Company’s information and data; and raising the awareness of information security on the clients, and the specific management measures are as follows:
| MANAGEMENT ITEM | MEASURE |
|---|---|
| Information Security Policy and Education Training | ● Formulate information security policy and raise information security awareness among employees through information security promotion |
| Network security management | ● Effectively manage the network environment according to operational requirements and security levels, and separate access control between internal and external network environments |
| System access control | ● Formulate system access control policy according to colleagues' business needs, specify the access authorization of users and personnel, and properly document the change process and preserve the records ● Separate the R&D from the general office environment to prevent unauthorized personnel from directly accessing confidential and sensitive data, and keep critical data from being disclosed |
| Terminal equipment management | ● Information security control for servers, PCs, and other devices, including software and hardware asset inventory, anti-virus, system patch update, and sensitive data access control |
| Data protection | ● Regularly schedule data preservation backups, including electronic files, documents, mail, server operating environment, personal computers, and network devices |
| Information Security Incident Management | ● Scan outsourced information system vulnerability and remedy vulnerability ● Provide solutions for unanticipated information security incidents, collect trace, and trace events to reduce the likelihood of occurrence and minimize operational impact |
Resources devoted to information security management and its implementation in 2023:
The Information Security Committee meets regularly on an annual basis to review and discuss implementation, with the most recent report to the Board of Directors being dated November 2, 2023. The information security incidents in 2023 did not affect the operations or goodwill of the Company, and ISO 27001 implementation and certification will be implemented in 2023.
- Information security training: All employees are included in the information security training program with an attendance of 100%.
- Information security incident treatment: No information security incidents happened, which have been constantly audited by the Information Security Unit to ensure the safety of the information communication environment.
- Information security member report: Every year, 1 meeting will be held and 1 information security policies have been newly issued.
- Weakness scan: Weakness scans have been conducted to reduce information security repairs by 46.37%.
- Information security publicity: 5 information security promotional campaigns have been launched to strengthen employees’ information security awareness.